Privileged Access Management Market worth $13.92 billion by 2030 - Exclusive Report by 360iResearch
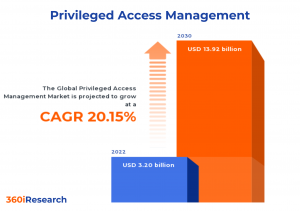
The Global Privileged Access Management Market to grow from USD 3.20 billion in 2022 to USD 13.92 billion by 2030, at a CAGR of 20.15%.
PUNE, MAHARASHTRA, INDIA , December 8, 2023 /EINPresswire.com/ -- The "Privileged Access Management Market by Component (Services, Solution), Deployment (Cloud, On-premise), Organization Size, End-Use - Global Forecast 2023-2030" report has been added to 360iResearch.com's offering.The Global Privileged Access Management Market to grow from USD 3.20 billion in 2022 to USD 13.92 billion by 2030, at a CAGR of 20.15%.
Request a Free Sample Report @ https://www.360iresearch.com/library/intelligence/privileged-access-management?utm_source=einpresswire&utm_medium=referral&utm_campaign=sample
Privileged Access Management is a comprehensive cybersecurity strategy designed to regulate, control, and monitor privileged users' access to critical information within a business network. The primary application of PAM is to restrict and monitor elevated access and privileged access within an IT environment. This helps prevent security breaches that may result from the misuse and exploitation of high-level access. PAM solutions are utilized across several industries, such as banking, financial services, insurance (BFSI), healthcare, retail, and energy, where data security is a high priority. The growing concern of cybersecurity threats and the need for effective data security solutions drive the demand for sophisticated privileged access management systems. The surge in digital transformation initiatives across various industries is also a significant factor contributing to the market growth. The lack of cybersecurity awareness among small and medium enterprises limits the market scope. Furthermore, technical complexities involved in the implementation and maintenance of PAM solutions often pose a challenge. The integration of machine learning and advanced analytics provides predictive capabilities and risk mitigation strategies. In addition, as more businesses transition to the cloud, the PAM market witnesses an increased demand for cloud-integrated PAM solutions.
Organization Size: Rising potential for cost-effective and sustainable PAM solutions across small and medium enterprises (SMEs)
Large enterprises feature complex organizational structures and vast networks, often spanning multiple regions. As a result, they necessitate robust PAM solutions to safeguard their diversified IT environments. Their preference veers more toward comprehensive, scalable, and highly secure solutions. SMEs, due to their typically smaller IT environments and fewer resources, prefer cost-effective, easy-to-deploy and manage PAM solutions. These enterprises also exhibit a rising demand for solutions that can be scaled as they grow.
Component: Expanding utilization of services associated with privileged access management to mitigate the risks of data breaches
The services offered under privileged access management include professional and managed services delivered by cybersecurity consulting companies. Professional services help businesses implement their PAM software and systems, whereas managed services manage these systems on an ongoing basis. The demand for these services has grown, given their role in mitigating the risks of data breaches from privileged accounts. PAM solutions refer to comprehensive platforms or software that manage and control privileged access in an organization. The need for PAM solutions has increased as organizations strive to secure critical systems against potential insider threats and external attacks, thereby ensuring business continuity. Identity management within PAM involves establishing and maintaining a centralized system for managing user identities, ensuring that only authorized individuals have access to privileged accounts. Access management, on the other hand, entails defining and enforcing policies to control user access rights and permissions.
Deployment: Growing adoption of cloud solutions that provide a quicker start with easier maintenance
Cloud deployment of PAM solutions offers an array of benefits, especially for businesses in the nascent stages or those looking for flexibility. The key advantage of cloud PAM solutions includes low upfront costs, as infrastructure components are hosted by the cloud service providers. Furthermore, cloud PAM allows for rapid deployment and scaling according to business requirements. On-premise deployment of PAM means setting up the infrastructure within the organization's premises. This deployment model offers a significant advantage, including full control over system configuration, security measures, and data storage.
End-User: Expanding the application of PAM across the healthcare industry to safeguard intellectual property and sensitive data
In the banking, financial services, and insurance (BFSI) sector, privileged access management (PAM) is crucial for managing sensitive financial data and ensuring compliance with various regulatory standards. Access to high-privileged accounts must be monitored and controlled to protect against potential insider threats or cyber breaches. The BFSI sector's PAM solutions have seen significant growth due to an increase in sophisticated cyber fraud and regulatory requirements. The energy & utilities sector requires rigorous PAM systems due to the prevalent cyber threats. Privileged access management prevents unauthorized access to critical infrastructure in the energy & utilities industry. Uncontrolled access can result in operational errors, safety concerns, or even sabotage. PAM helps ensure that only the right individuals can access critical systems and that every action taken is logged and traceable. The IT & telecom sector demands advanced PAM solutions due to vast data networks and infrastructure. The information technology & telecommunication sector deals with a large volume of data and often faces increased cybersecurity risks. In the healthcare industry, protecting patient information is paramount for legal, ethical, and operational reasons. PAM helps to ensure that only authorized healthcare staff can access sensitive patient data and medical records. Privileged access management helps in controlling and restricting access to sensitive data and systems. It ensures that only authorized personnel can access and modify critical network resources. The advent of Industry 4.0 demands robust PAM provisions in manufacturing. Manufacturing companies often use PAM to safeguard intellectual property and product design documents. PAM helps mitigate the risk of data theft and ensures that rights are granted only on a 'need-to-know basis'. In addition, PAM's centralized access control machinery assists in maintaining operational control and security over various production systems and processes. In the retail & eCommerce sector, customer data protection is of utmost importance. In the retail & eCommerce sectors, PAM is vital for protecting customer data and ensuring secure online transactions. It plays a vital role in preventing data breaches that could lead to financial loss and reputational damage.
Regional Insights:
In the Americas, the United States and Canada are leading the charge in implementing progressive privileged access management solutions. A notable increase in awareness about cybersecurity issues, shaping customer purchasing behavior across the region. Software companies in the American region have been heavily investing in privileged access management solutions. The proliferation of privileged access management is particularly visible within governmental institutions. EU countries lead in privileged access management solutions adoption; the Middle East exhibits the highest growth rates in the region. Africa, though relatively slow in the adoption of privileged access management solutions, holds vast growth potential due to its emerging markets. Notable initiative includes the EU-funded project, which enhances cloud security with advanced privileged access management solutions implementations. In the APAC, Japan, India, and China governments initiative prioritizes cybersecurity research, offering promising opportunities for advanced privileged access management solutions. APAC is showing robust growth due to increased demand from the burgeoning IT sector. The significant shift in customer purchasing behavior towards advanced cybersecurity solutions positioning the Asia Pacific region as pivotal in the global PAM market.
FPNV Positioning Matrix:
The FPNV Positioning Matrix is essential for assessing the Privileged Access Management Market. It provides a comprehensive evaluation of vendors by examining key metrics within Business Strategy and Product Satisfaction, allowing users to make informed decisions based on their specific needs. This advanced analysis then organizes these vendors into four distinct quadrants, which represent varying levels of success: Forefront (F), Pathfinder (P), Niche (N), or Vital(V).
Market Share Analysis:
The Market Share Analysis offers an insightful look at the current state of vendors in the Privileged Access Management Market. By comparing vendor contributions to overall revenue, customer base, and other key metrics, we can give companies a greater understanding of their performance and what they are up against when competing for market share. The analysis also sheds light on just how competitive any given sector is about accumulation, fragmentation dominance, and amalgamation traits over the base year period studied.
Key Company Profiles:
The report delves into recent significant developments in the Privileged Access Management Market, highlighting leading vendors and their innovative profiles. These include Arcon, BeyondTrust Corporation, Blue Star Limited, Bravura Security Inc. by Volaris Group, Broadcom Inc. by Avago Technologies Limited, Cyberark Software Ltd., Delinea Inc., Devolutions, Fortra, LLC, Fudo Security sp. z o.o, International Business Machines Corporation, Iraje Inc., Kron Teknoloji A.Ş., Lenovo Group Limited, Microsoft Corporation, Nomura Research Institute, Ltd. by Nomura Holdings, Inc., One Identity LLC by Quest Software Inc., Open Text Corporation, Osirium Ltd. by SailPoint Technologies, Inc., Sectona Technologies Pvt. Ltd., Senhasegura, Silverlake Mastersam, Simeio Solutions, LLC, WALLIX Group, and Zoho Corporation Pvt. Ltd..
Inquire Before Buying @ https://www.360iresearch.com/library/intelligence/privileged-access-management?utm_source=einpresswire&utm_medium=referral&utm_campaign=inquire
Market Segmentation & Coverage:
This research report categorizes the Privileged Access Management Market in order to forecast the revenues and analyze trends in each of following sub-markets:
Based on Component, market is studied across Services and Solution. The Services is further studied across Consulting, Implementation & Integration, Professional Services, and Support & Maintenance. The Solution is further studied across Access Management, Identity Management, and Session Monitoring & Management. The Solution is projected to witness significant market share during forecast period.
Based on Deployment, market is studied across Cloud and On-premise. The Cloud is projected to witness significant market share during forecast period.
Based on Organization Size, market is studied across Larger Enterprises and Small and Medium Enterprises (SMEs). The Larger Enterprises is projected to witness significant market share during forecast period.
Based on End-Use, market is studied across BFSI, Energy & Utilities, Healthcare, IT & Telecom, Manufacturing, and Retail & eCommerce. The Healthcare is projected to witness significant market share during forecast period.
Based on Region, market is studied across Americas, Asia-Pacific, and Europe, Middle East & Africa. The Americas is further studied across Argentina, Brazil, Canada, Mexico, and United States. The United States is further studied across California, Florida, Illinois, New York, Ohio, Pennsylvania, and Texas. The Asia-Pacific is further studied across Australia, China, India, Indonesia, Japan, Malaysia, Philippines, Singapore, South Korea, Taiwan, Thailand, and Vietnam. The Europe, Middle East & Africa is further studied across Denmark, Egypt, Finland, France, Germany, Israel, Italy, Netherlands, Nigeria, Norway, Poland, Qatar, Russia, Saudi Arabia, South Africa, Spain, Sweden, Switzerland, Turkey, United Arab Emirates, and United Kingdom. The Americas commanded largest market share of 38.75% in 2022, followed by Europe, Middle East & Africa.
Key Topics Covered:
1. Preface
2. Research Methodology
3. Executive Summary
4. Market Overview
5. Market Insights
6. Privileged Access Management Market, by Component
7. Privileged Access Management Market, by Deployment
8. Privileged Access Management Market, by Organization Size
9. Privileged Access Management Market, by End-Use
10. Americas Privileged Access Management Market
11. Asia-Pacific Privileged Access Management Market
12. Europe, Middle East & Africa Privileged Access Management Market
13. Competitive Landscape
14. Competitive Portfolio
15. Appendix
The report provides insights on the following pointers:
1. Market Penetration: Provides comprehensive information on the market offered by the key players
2. Market Development: Provides in-depth information about lucrative emerging markets and analyzes penetration across mature segments of the markets
3. Market Diversification: Provides detailed information about new product launches, untapped geographies, recent developments, and investments
4. Competitive Assessment & Intelligence: Provides an exhaustive assessment of market shares, strategies, products, certification, regulatory approvals, patent landscape, and manufacturing capabilities of the leading players
5. Product Development & Innovation: Provides intelligent insights on future technologies, R&D activities, and breakthrough product developments
The report answers questions such as:
1. What is the market size and forecast of the Privileged Access Management Market?
2. Which are the products/segments/applications/areas to invest in over the forecast period in the Privileged Access Management Market?
3. What is the competitive strategic window for opportunities in the Privileged Access Management Market?
4. What are the technology trends and regulatory frameworks in the Privileged Access Management Market?
5. What is the market share of the leading vendors in the Privileged Access Management Market?
6. What modes and strategic moves are considered suitable for entering the Privileged Access Management Market?
Read More @ https://www.360iresearch.com/library/intelligence/privileged-access-management?utm_source=einpresswire&utm_medium=referral&utm_campaign=analyst
Mr. Ketan Rohom
360iResearch
+1 530-264-8485
ketan@360iresearch.com
Legal Disclaimer:
EIN Presswire provides this news content "as is" without warranty of any kind. We do not accept any responsibility or liability for the accuracy, content, images, videos, licenses, completeness, legality, or reliability of the information contained in this article. If you have any complaints or copyright issues related to this article, kindly contact the author above.