(Video) Iranian Regime Tactics Against Its Principal Opposition, MEK – Part 2

The following is the second part of a piece written by former MEP Struan Stevenson in the book “Iran Democratic Revolution,” published by the International Committee in Search of Justice (ISJ).
The MEK is strictly demonized, by the regime and delegitimizes, and invalidates the entire resistance movement inside and outside Iran. This sophisticated vilification campaign has been multi-faceted, well-funded, and extensive as a matter of state policy.
The Iranian government and its intelligence apparatus consider the MEK the most serious dissident organization with regard to the Revolution.” the regime uses its vast resources to deploy a cyber army for a demonization campaign against the MEK.
Mr.Stevenson, “The MOIS portray the opposition in a negative light and describes them as terrorists. The MOIS is particularly active in the field of anti-MEK "
Demonization
Another attempt by the regime to confront the MEK is to strictly demonize, delegitimize, and invalidate the entire resistance movement inside and outside Iran. This sophisticated vilification campaign has been multi-faceted, unrelenting, well-funded, and extensive as a matter of state policy.
It relies on fabricated and well-orchestrated messaging and narratives promoted by “former members” of the People’s Mojahedin Organization of Iran (PMOI / MEK), guided commentary by fake “opponents” of the regime, and Tehran’s burgeoning cyber army in the virtual world.
For years, the regime has employed the services of so-called former MEK members who defected years or decades ago. According to a US Library of Congress report in December 2012: “From 1990– 93, [the Iranian regime’s Ministry of Intelligence and Security] MOIS recruited former members of the Mojahedin-e-Khalq (MEK)—also known as the People’s Mujahedin of Iran (PMOI) or MKO— in Europe and used them to launch a disinformation campaign against the MEK.
The Iranian government and its intelligence apparatus consider the MEK the most serious dissident organization with regard to the Revolution.”12 The report adds: “Ali Younesi, the former minister of intelligence and security, reported on state television in October 2004 that the ministry’s Department of Disinformation had hired thousands of agents, including some former MEK members, to boost the department’s function.” 13
The report draws attention to two clear cases regarding these so-called “former MEK members,” publishing their pictures and revealing the MOIS policy in this regard:
“The recruitment of a British subject, Anne Singleton, and her Iranian husband, Masoud Khodabandeh, provides a relevant example of how the MOIS coerces non-Iranians to cooperate. She worked with the MEK in the late 1980s. Masoud Khodabandeh and his brother Ibrahim were both members of the MEK at the time. In 1996 Masoud Khodabandeh decided to leave the organization. Later, he married Anne Singleton. Soon after their marriage, the MOIS forced them to cooperate by threatening to confiscate Khodabandeh’s mother’s extensive property in Tehran. Singleton and Khodabandeh then agreed to work for the MOIS and spy on the MEK.”
Judicial and security officials in Europe have shown, based on concrete evidence, that these “former members” are involved in malicious activities and disinformation against the MEK guided strictly by the regime’s intelligence and terrorist agencies.
For example, Albania’s police chief announced in October 2019 the disruption of a terrorist network controlled by the regime that intended to harm the MEK and its members.
He said Alireza Naghashzadeh, an agent of Iran’s Ministry of Intelligence and Security (MOIS), was involved in this terrorist operation. Naghashzadeh identifies himself as a “former member” of the MEK.
In April 2016, German authorities arrested Meysam Panahi, who claimed to be a former MEK member, for spying on the MEK and the National Council of Resistance of Iran (NCRI) .16 He was sentenced to over two years in prison. Court proceedings revealed that Panahi operated under orders from a senior intelligence officer based in Tehran and identified as Sajjad.
In 2022, the Albanian media reported that authorities had detained and interrogated 20 Iranian nationals on charges of espionage in the service of the regime’s intelligence services. These individuals were accused of “receiving money from Iran’s secret services, the Quds Force, and the IRGC to obtain information about the MEK in Albania.”
This ring was comprised of “former members” of the MEK recruited by the regime’s intelligence service. Tellingly, the anti-MEK ring runs out of Tehran and residing in Albania was able to dupe or manipulate a dozen journalists from such news media sources as The Guardian, Foreign Policy, The Independent, Der Spiegel, MSNBC, and even the BBC and the New York Times, as well as others, to publish derogatory and outlandish accusations against the MEK.
The 80/20 rule
The regime’s other method to demonize the MEK is using individuals who identify themselves as “opponents”, to criticize the MEK. Cognizant of the fact that its own propaganda against the MEK would have little if any, chance of success in undermining the Resistance’s international standing, Tehran devised what is commonly known within the Iranian diaspora as the 80/20 rule for those who sought its favor.18 This tactic means that so-called “opponents” focus eighty percent of their criticism on the obvious and unavoidable, including mild or implied criticism of the regime, in order to establish credibility.
They then target the MEK for the remaining twenty percent of the time, pushing Tehran’s propaganda line. This tactic is meant to lend a measure of credibility to the anti-MEK propaganda, supposedly because it is coming from those who at first glance cannot be dismissed as regime agents.
An example is Mehrdad Arefani. Sentenced by a Belgian court to a 17-year imprisonment term in February 2021 for his role in the attempted bombing of the NCRI annual gathering in 2018, Arefani started to cooperate with the regime while in prison in Iran. He was later sent to Europe. He claimed to be a poet, a human rights activist, and even an atheist in order to distance himself from the regime.
He even launched a campaign against Iranians visiting Iran to gain credibility as an opponent of the regime. He claimed to be a political sympathizer of the MEK and acted as a sleeper cell and intelligence asset of the regime for nearly 18 years. In a report to a Belgian tribunal, the Belgian State Security wrote:
“The MOIS continues to portray the opposition in a negative light and describes them as terrorists. The MOIS is particularly active in the field of anti-MEK (Mujahedin-e Khalq, Iranian opposition group) propaganda in the European Parliament.”
The ultimate objective of the regime’s demonization and vilification campaign is to set the stage for the execution of terrorist plots against the Iranian Resistance. Arefani, for example, had carried out all his activities and preparations as the groundwork for a large-scale terrorist plot.
The cyber army
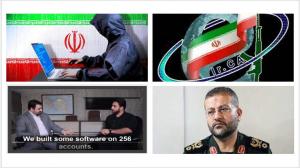
Finally, the regime uses its vast resources to deploy a cyber army as yet another prong in its demonization campaign against the MEK. According to a report by the Center for Strategic and International Studies on June 25, 2019,19 three military organizations were playing leading roles in cyber operations:
the Iranian Revolutionary Guard Corps (IRGC), the Basij, and Iran’s ’Passive Defense Organization (NPDO).’”
In a striking admission in May 2022, Ruhollah Momen Nasab, a former commander of Tehran’s cyber army, provided a glimpse of its operations and said:
“We created new accounts on Twitter, using the persona of other Twitter influencers who were mainly counter-revolutionary activists. Ours just differed in a single character and was quite similar to the real one. We used the same picture and the same name, but everything was fake. Once created, we started our activities.”
On November 4, 2019, the regime posted fake stories about the MEK. It used a fake Twitter account of Alexis Kohler,21 Secretary- General of the office of French President Emmanuel Macron in the Elysée Palace, claiming that “The Secretary-General of the French Presidency has announced that the People’s Mojahedin (PMOI/MEK) will soon be driven from France.” The next day, the Elysée denied this statement, adding that the senior official did not even have a Twitter account.
On Twitter, and all three dramatically increased the rate of anti-MEK posts after the mid-July 2022 cyberattack became public.”
Now that the instrumental and expanding role of the MEK and its Resistance Units have become increasingly threatening for the regime, Tehran has become even more focused on its demonization campaign against the movement.
Persistent and systematic attacks and lies against the MEK are critical as far as the regime is concerned. Not least because the MEK has a leading role in organizing the protests. Moreover, the mullahs are keenly aware that the MEK and the NCRI are the most viable alternatives to their rule. During an unprecedented nationwide uprising, a weakened and desperate regime is utilizing every means at its disposal, including “former members,” “opponents,” and a cyber army to confront the MEK’s rising popularity and organizational prowess in the hopes of countering the powerful tides of the uprising.
On December 10, 2020, Treadstone 71, a California-based independent cyber intelligence company, released details of an Iranian influence operation.22 It said: “The IRGC Cyber Units triggered core team members with military precision aimed at the National Council of Resistance of Iran (NCRI) annual online conference. The IRGC, MOIS, and low-level Basij Cyber Units flooded Twitter with nearly one hundred twelve thousand tweets over sixty hours using hashtags and content intent on controlling the social media narrative.”
More recently, in September 2022, Microsoft was asked to investigate a destructive cyber-attack against the Albanian government in mid-July. The tech giant said in a report: “The messaging, timing, and target selection of the cyberattacks bolstered our confidence that the attackers were acting on behalf of the Iranian government.”23 Microsoft added:
“Ahead of the cyberattack, on June 6, Ebrahim Khodabandeh, a disaffected former MEK member posted an open letter addressed to Albanian Prime Minister Edi Rama warning of the consequences of escalating tensions with Iran. Invoking ‘[h]acking of Tehran municipal systems’ and ‘gas stations,’ Khodabandeh claimed that the MEK was the source of ‘sabotaging acts against the interests of the Iranian people [sic]’ and argued that these constituted ‘the hostile work of your government’ and has caused “obvious enmity with the Iranian nation [sic].’”
The comprehensive and detailed Microsoft report also said: “In May 2021, at around the same time that Iranian actors began their intrusion into Albanian government victim systems, accounts for two anti-MEK social media personas, which do not appear to correspond to real people, were created on both Facebook and Twitter." The accounts largely post anti-MEK content and engage with the social media accounts of some of the individuals detailed above. These two accounts along with a third, older account, were among the first to promote posts from Homeland Justice accounts.
Shahin Gobadi
NCRI
+33 6 61 65 32 31
email us here
On Saturday, June 30, 2018, the Iranian Resistance’s grand gathering was held in Paris, France.
Legal Disclaimer:
EIN Presswire provides this news content "as is" without warranty of any kind. We do not accept any responsibility or liability for the accuracy, content, images, videos, licenses, completeness, legality, or reliability of the information contained in this article. If you have any complaints or copyright issues related to this article, kindly contact the author above.